OpenMethods allows users to log in with a single sign-on (SSO) system using SAML 2.0.
An identity provider (IDP) that supports SAML 2.0 can be set up in various ways, such as a self-hosted Active Directory Federation Services (ADFS) server. ADFS is a Microsoft service that provides web login using existing Active Directory credentials.
This guide uses screenshots from Windows Server 2019 and AD FS Management Version: 10.0.0.0, but you should be able to perform similar steps on other versions.
To begin, you need to install ADFS on your server. However, the installation and configuration of ADFS are beyond the scope of this guide. You can find detailed information about it in this Microsoft article.
During testing, ensure that your workstation authentication is set to the same test email you use for the test. Otherwise, ADFS will not allow you to log in, even if the configuration and profile are correct.
💡 We strongly recommend configuring SSO in your browser's separate incognito mode window. This way, you can keep the session in the standard window, allowing you to switch off the SSO authorization in case of a misconfiguration.
The Values required
Please make sure to correctly configure the Provider settings in the OpenMethods Experience Cloud.
-
Certificate
- The certificate value is copied from the instructions below.
-
Issuer
- https://<ADFS Server domain>
-
Sign In URL
- https://<ADFS Server domain>/adfs/ls
-
Sign Out URL
- https://<ADFS Server domain>/adfs/ls
Open the AD FS Management Console, click Add Relying Party Trust… in the Actions pane, and click Start on the wizard introduction page.
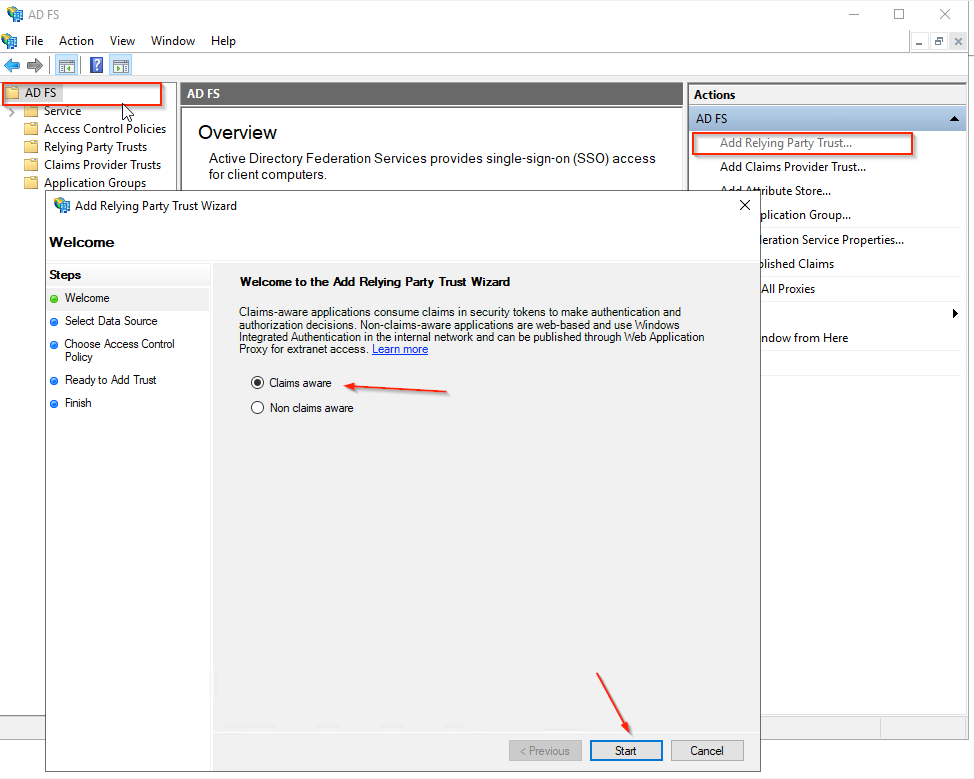
- Select Enter data about the relying party manually
- Click the Next button.
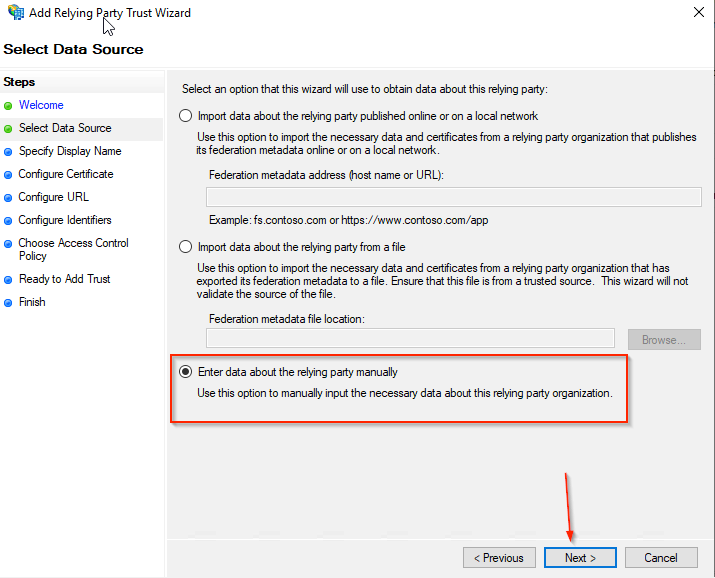
- Enter a Display name; the suggested name is OpenMethods-SSO
- Click the Next button.
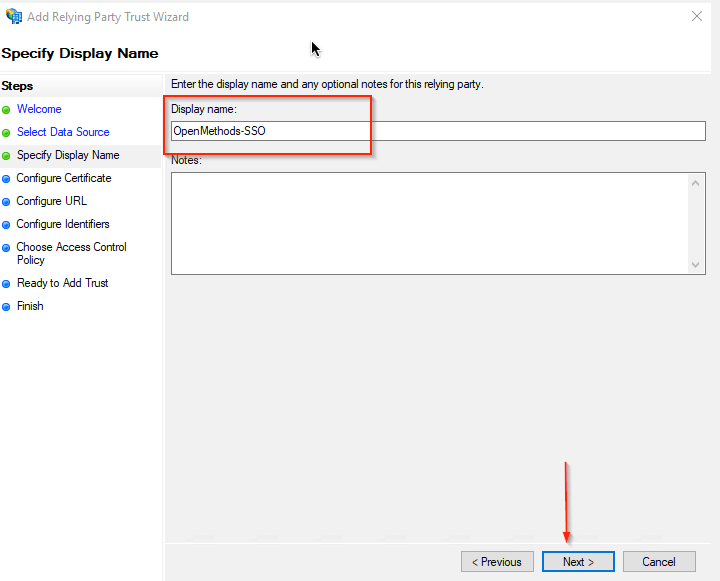
- A token encryption certificate is not needed, so Click Next to continue.
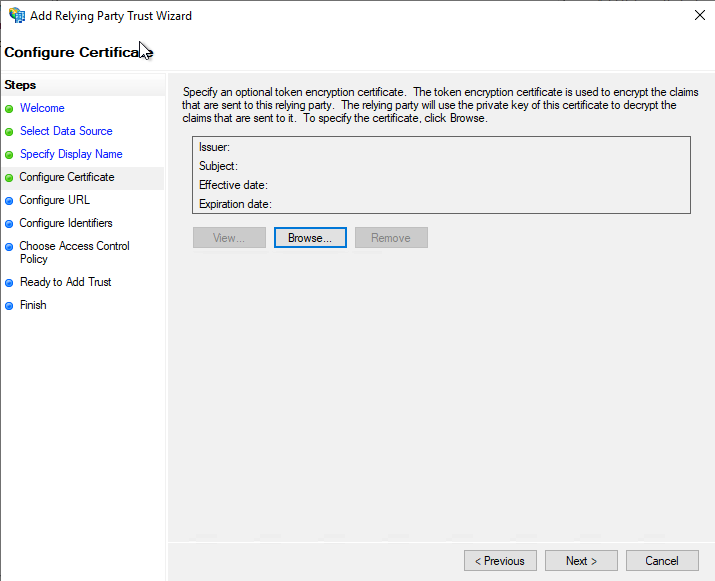
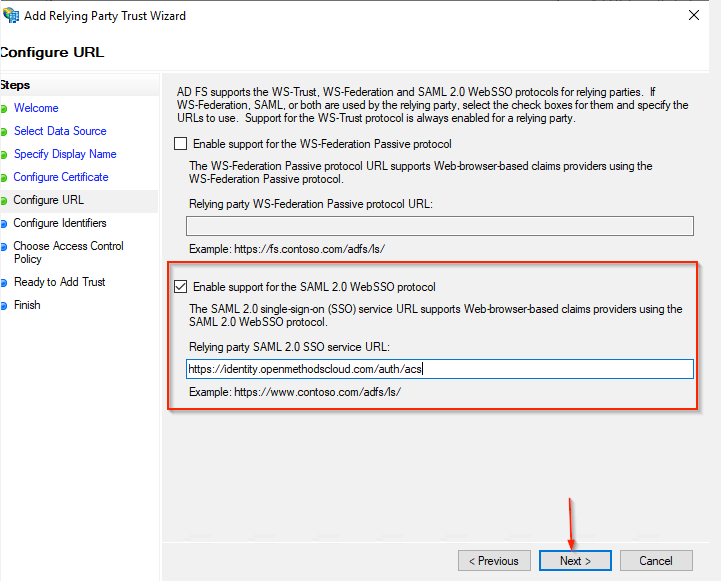
- Click the check box, Enable support for the SAML 2.0 Web SSO protocol
- Enter the URL - https://identity.openmethodscloud.com/auth/acs in the Relying party SAML 2.0 service URL text box
- Click the Next button.
- Enter https://<Your ADFS server domain>.com in the Relying party trust identifier.
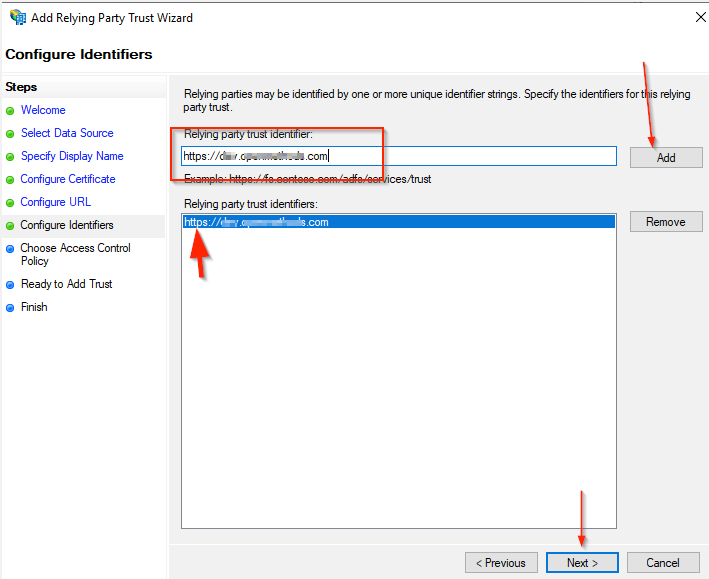
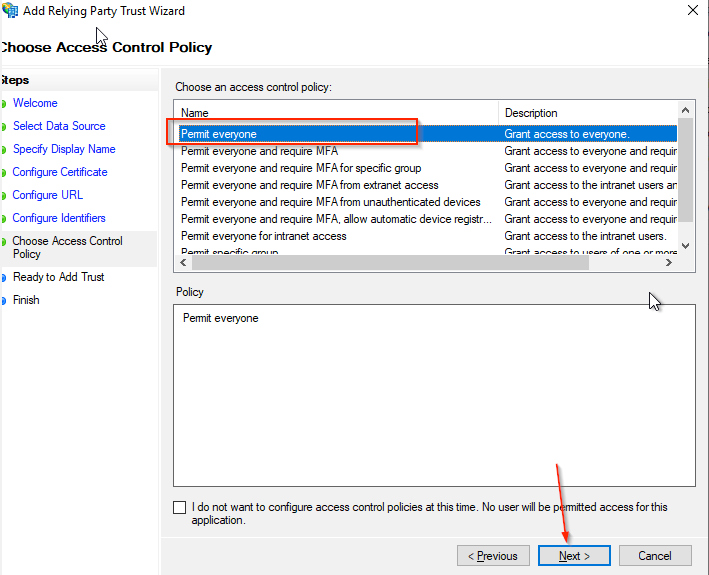
- Select Permit everyone in the Choose an access control policy
- Click the Next button.
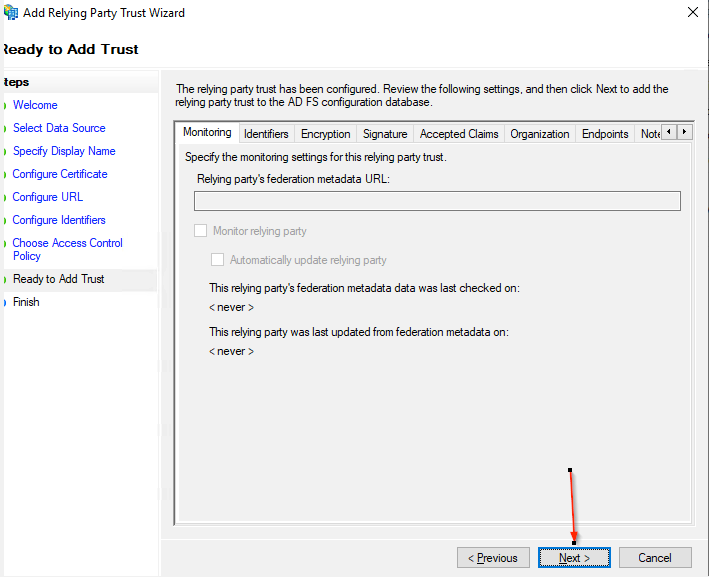
- Review your settings
- Click the Next button.
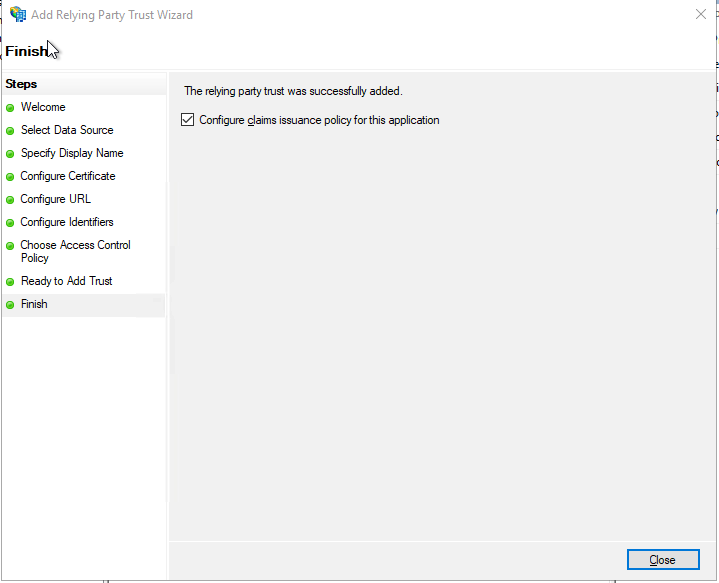
- Click Close to finish the wizard.
- Keep the Configure claims issuance policy selected for this application.
- After closing the wizard, the Edit Claim Issuance Policy for OpenMethod-SSO window will be opened.
- Click Add Rule… on the Issuance Transform Rules tab.
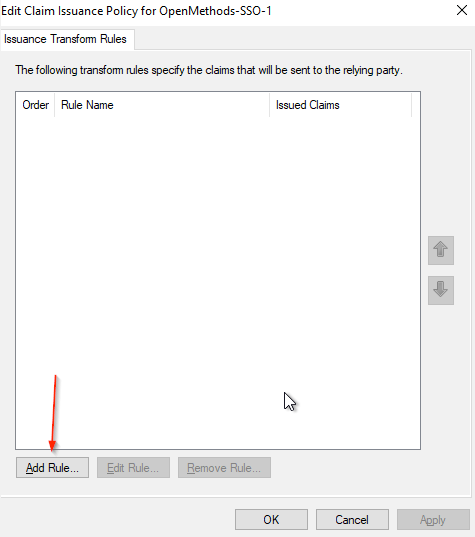
- Select Send LDAP Attributes as Claims from the Claim rule template drop-down
- Click the Next button.
Attribute Mappings
- Enter a Claim rule name, such as Get Attributes, then
- Set the Attribute Store to Active Directory,
- Type or select E-Mail-Addresses as LDAP Attribute, and
- Type emailaddress as Outgoing Claim Type.
- Add the following from the table and click Finish.
Note: After you begin typing in the specified value, it is essential to select the options with the same dashes and spaces documented. The integration may not work if you select a variant that does not match exactly.
Active Directory as your attribute store, map as follows:
LDAP Attribute |
Outgoing Claim Type |
|---|---|
| E-Mail-Addresses | emailaddress |
| Given-Name | firstname |
| Surname | lastname |
| Display-Name | name |

- Click Add Rule… on the Issuance Transform Rules tab again
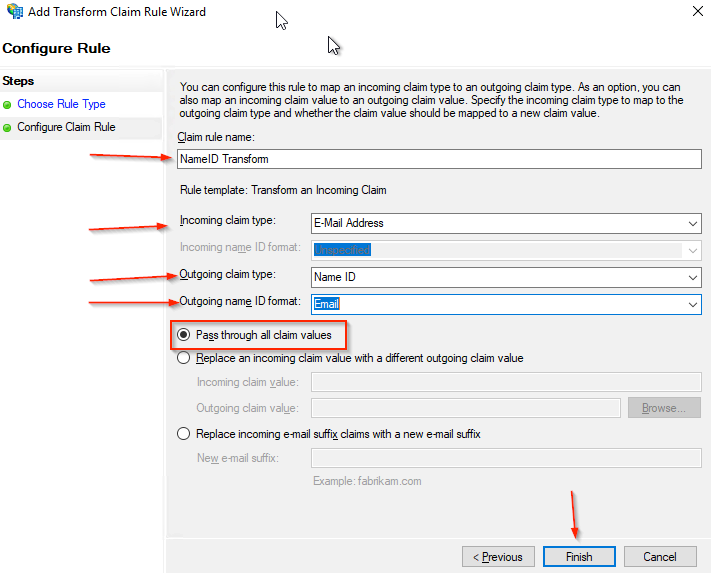
- Select Transform an Incoming Claim
- Click the Next button.
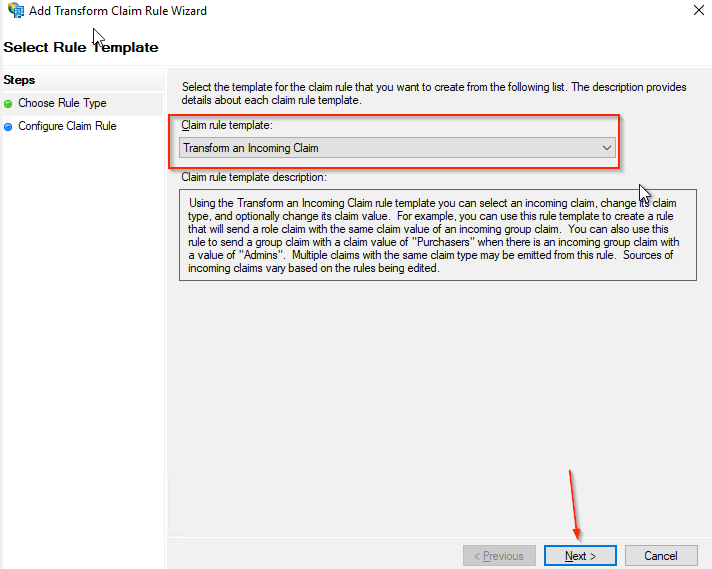
- Enter a Claim rule name, such as NameID Transform
- Select Incoming claim type to E-Mail Address
- Select Outgoing claim type to Name ID and then
- Select Email as Outgoing name ID format.
- Select Pass through all claim values.
- Click the Finish button.
- Click OK to close the Edit Claim Rules window.
- We can add new rules or Edit rule Attributes by opening the Claims Rules window as shown in the image.
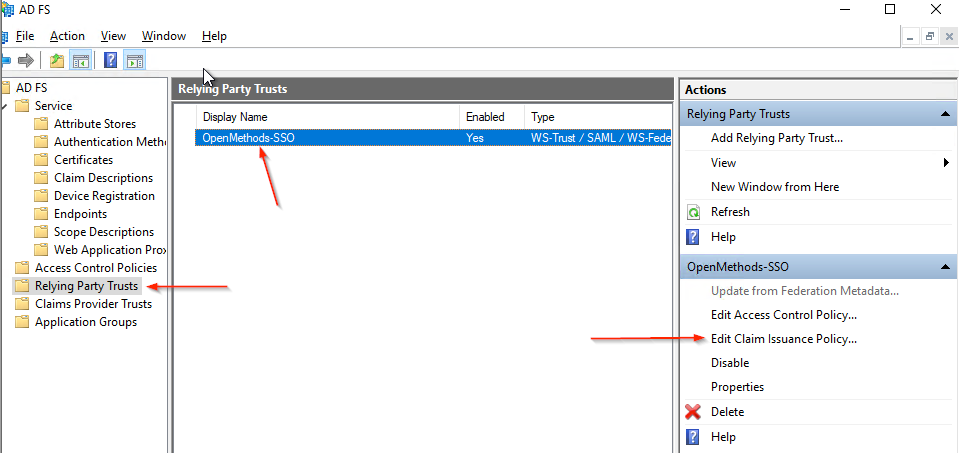
- Go to Services > Certificates,
- Select Token-signing certificate and
- Click View Certificate… from the Action pane.
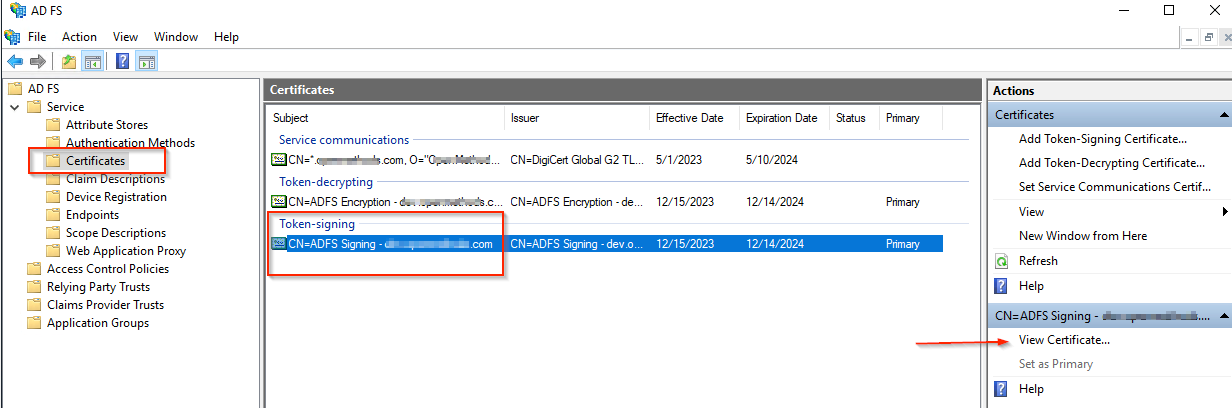
- Click the Details tab
- Click the Copy to File…
- Click the OK button.

- Certificate Export Wizard will open now.
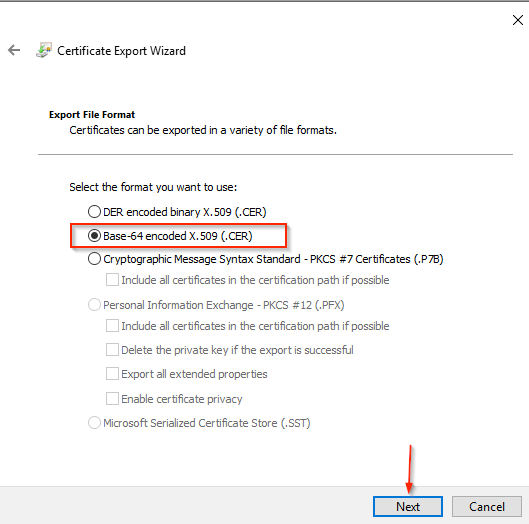
- Click Next button
- Select Base-64 encrypted X.509 (.CER)
- Click the Next button.
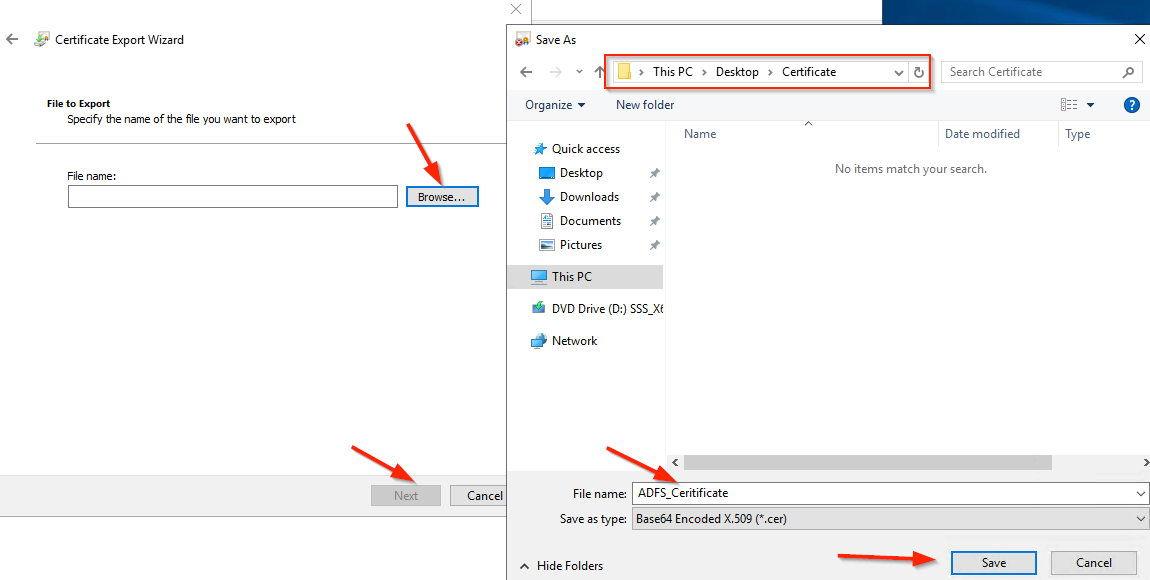
- Choose a location and enter a file name to save the certificate file
- Click Save button
- Click the Next button.
- Click the Finish button to close the wizard.
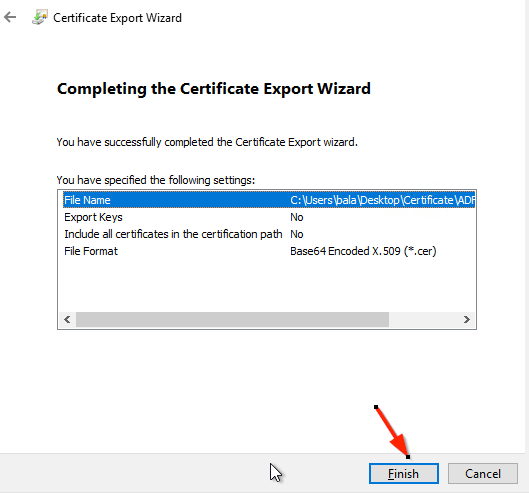
- Open the Certificate file in a Notepad copy the whole content, and paste it into the Certificate text in the OpenMethods SSO Provider configuration.
- With this, the configuration to ADFS has been completed!
- After this, add the ADFS configuration to the OpenMethods Experience Designer section and enable ADFS SSO for the Admin users.